Security Policy
This page lists the most common questions regarding security and the rules implemented at Kraaft. By default, we apply the majority of the standards set by the large groups we work with to all of our clients. If you have any questions, please contact our CISO at security@kraaft.co or on +33 (0)1 84 60 64 68.
☁️ Where is customer data hosted?
1. We use the NoSQL Firestore database, which has the advantage of being a mobile-oriented, real-time and offline database. Firestore manages the storage of part of the data in the phone's cache to provide an “offline” data consultation experience. We have three storage components: Firebase authentication, Firestore (real-time BDD), and Google Cloud Storage (files)
2. The data is stored at GCP (Google Cloud Platform) on multi-tenant platforms: St Ghislain (Belgium) and Eemshaven (Netherlands). Google manages data replication and guarantees very high availability.
3. The physical security of the servers is guaranteed by the SOC2 certificate of Google servers https://cloud.google.com/security/compliance/soc-2?hl=frhttps://cloud.google.com/security/compliance/soc-2?hl=fr
4. Architecture and data hosting diagram at KRAAFT
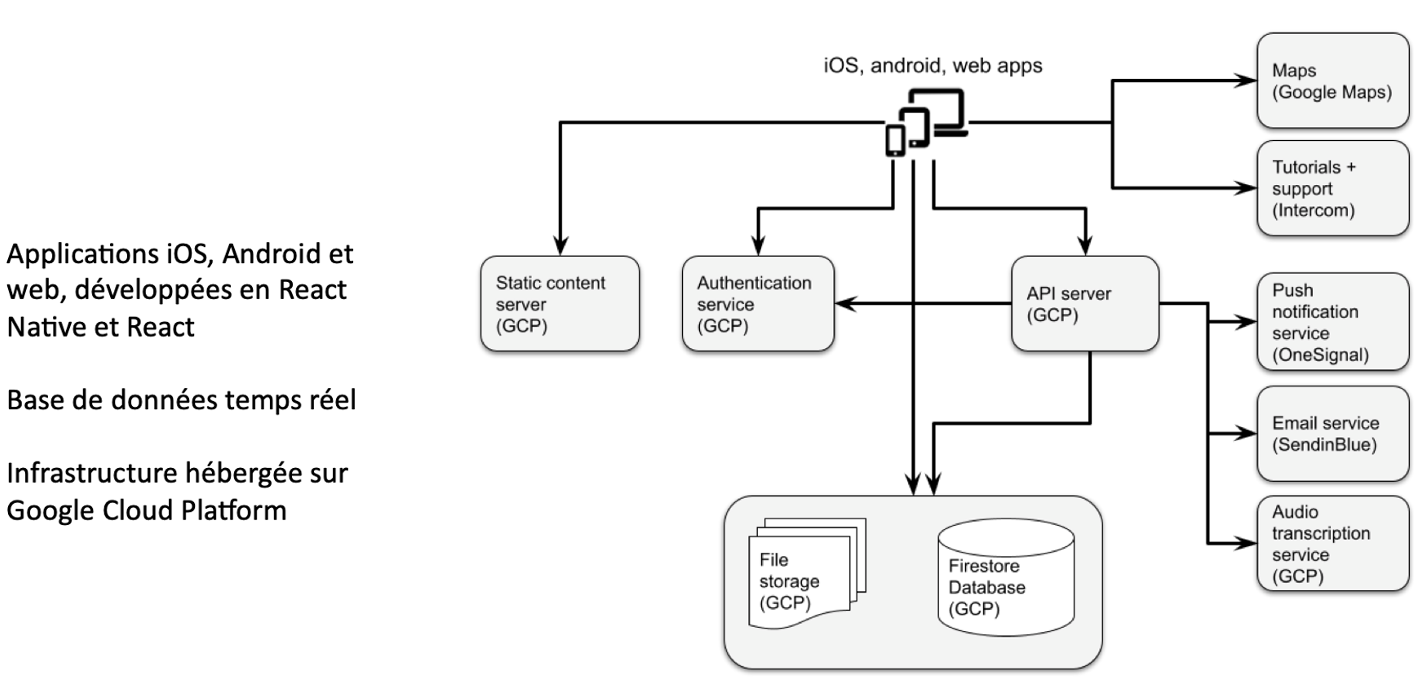
🆔 Identity and Access Management (IAM)
5. All connections to the Kraaft application are encrypted in transit via SSL/TLS, ensuring the confidentiality and integrity of all web requests and guaranteeing that all information is transmitted securely to our servers.
6. All access to the Kraaft application (except access to the login and registration pages) is secured by authentication (email/password, telephone or SSO) and any request made by the application to our servers is secured by authentication tokens.
7. The Customer will inform its End Users about the processing of their personal data by Kraaft. Kraaft's privacy policy applicable to this treatment is available here: www.kraaft.co/confidentialite
8. Our platform offers role-based access control (RBAC) capabilities. This system allows a segregation of tasks based on access control, fine and applied within an organization. See role details here: https://help.kraaft.co/fr/articles/6845358-les-roles-qui-peut-faire-quoi
9. Unique and Personal Identifiers: Each user of the Kraaft platform is assigned a unique and personal identifier (based on their email or telephone number). Shared accounts are prohibited in order to ensure clear traceability and responsibility for each action performed on the platform.
🦾 Accessibility guarantees (SLAs)
10. We make our best efforts to ensure that the Solution is accessible 24/7, with the exception of preventive and corrective maintenance periods. Our GCP host guarantees very high availability.
11. We notify as much as possible 48 hours in advance in the event of maintenance and interruption of service.
12. Outside of Preventive Maintenance periods, Kraaft guarantees the following levels of commitment (SLA): - RTO (Recovery Time Objective) or Maximum Recovery Time of 48 hours- and RPO (Recovery Point Objective) or Maximum Data Loss of 24 hours
13. The processes we have in-house make it possible to limit bugs in production despite monthly updates:
13.1. Developers participate in part of the product workshops, and do not discover user stories (US) at the last moment; they establish technical specifications that are validated by several people;
13.2. Unit tests are implemented on almost all new bricks and e2e tests cover critical paths;
13.3. A QA is done for each feature and for each update of the application;
13.4. Each release is created a “Release procedure”, which summarizes all the information necessary for the smooth running (possible migration scripts, adding/modifying environment variables);
13.5. Implementation of Continuous Integration (CI)/Continuous Development (CD) workflows that automate deployments on the Web and to the App Stores;
14. We have set up a dashboard for reporting error logs.
15. We automatically monitor any security issues in our infrastructure and apply the necessary patches.
16. We protect our web applications by filtering malicious web traffic based on IP addresses, HTTP headers, HTTP body, or URI strings, which helps block common attack patterns, such as SQL injection or cross-site scripting. We have also taken steps to implement protection against DDoS and MITM attacks via highly available load balancers and robust SSL/TLS infrastructure.
📀 Data Loss Prevention Policy (DLP)
17. Our Data is automatically backed up daily with a retention period of 30 days.
18. Upon expiration or termination of the Agreement, Kraaft undertakes to return to the Customer or to delete all Customer Data in its possession. Kraaft has set up a data reversibility procedure: at the Customer's request, Kraaft can retrieve and share a JSON file that contains all the Customer Data in its possession.
19. The request procedure is described in article 7 “Reversibility” of the CGV (www.kraaft.co/cgv); we undertake to respond to the request by email within 24 hours (1 working day) and to carry out the processing in an additional 72 hours (3 working days).
20. On a construction site, it is always possible for a user to extract data (i) from the entire site (ii) or from a specific event/form. Extraction format: Word file, or.zip folder containing photos and documents.
21. Our Disaster Recovery Plan (DRP) is tested annually.
🧠 Ownership and use of data
22. Any data provided by the customer to Kraaft belongs to the customer (“Customer Data”). The construction photos that are shared on Kraaft cannot be used by our teams for commercial purposes.
23. The Customer grants Kraaft the right to access and use Customer Data for the purposes of carrying out its obligations: typically for your customer manager to help you if you have a problem.
24. Kraaft grows over time using a variety of data points, including Usage Data, Analytics Data, and Customer Data (collectively, “Solution Data”). As such, the customer accepts that Kraaft owns all rights, titles and interests in the Solution data. Typically, if you take picket photos on Kraaft, and we develop a network detection report module, you will be the owner of the photos and Kraaft the owner of the module.
25. Our privacy team will be happy to answer all your questions and requests. You can contact them at dpo@kraaft.co. We are supported by the specialized firm Dipeeo on these subjects.
🇪🇺 RGPD
26. Kraaft undertakes to process all the information made available to it as part of its activities in accordance with the regulations in force [Compliance with the protection of personal data (law No. 78-17 of 6 January 1978, and its evolutions) as well as Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016, relating to the protection of natural persons with regard to the processing of personal data and to the free movement of such data, and repealing Directive 95/46/EC], and to specific contracts with its customers.
27. Kraaft declares that its Services were created in compliance with the rules of “Privacy by design” and “Privacy by default” and therefore that they are accompanied by functionalities allowing the Customer to comply with its obligations as data controller.
28. Kraaft undertakes to use the Customer's personal data only in connection with the use of its Services and only on documented instructions from the latter.
29. Kraaft undertakes to notify the Customer, in accordance with the obligations provided for in article 28 of the RPGD, as soon as possible after becoming aware of it, any personal data breach that may concern the Customer's personal data.
30. The Subcontractor declares that all internal or external personnel required to process the Customer's personal data are committed by a confidentiality clause, an information systems charter or any other binding legal act and are regularly the subject of training and awareness-raising.
🔐 ISO 27001 certification
31. Kraaft is ISO/IEC 27001:2022 certified, demonstrating our commitment to best practices in information security. This international certification validates the robustness of our Information Security Management System (ISMS).
32. The scope of certification covers the technical infrastructure, applications and systems that ensure the delivery of our cloud product services to our customers, as well as all technical activities that hold, obtain, share or manage customer and business data, and the HR, Engineering, and Systems business functions HR, Engineering, and Systems that ensure the delivery of our cloud product services to our customers, as well as all technical activities that hold, obtain, share or manage customer and business data, and Finance, and Finance.
33. Our certification is issued by INTERCERT (registration number: IC-IS-2505209) and can be verified on their official portal: https://www.intercert.com/customers/certification-verification
34. This certification is subject to annual surveillance audits and recertification every three years, guaranteeing the continuous maintenance of our security standards at the highest level.
👔 How to limit human risks?
35. Two contact persons related to Security are appointed at Kraaft. The first, Cédric BOIDIN (cedric@kraaft.co, Technical Director), is the point of reference for the implementation of new solutions or technical documentation. The second, Marc NEGRE (marc@kraaft.co, Developer and Product Director), is responsible for raising awareness among the teams, i.e. he ensures consistency between the actions taken, the technical documentation, and the understanding of the challenges by the teams.
36. Kraaft has set up a phishing awareness program with the MANTRA software (https://fr.mantra.ms). As a reminder, phishing is the first cyber attack vector according to ANSSI and human vulnerability is the easiest way to hack an organization. The platform allows us to train and train our teams through phishing simulations.
37. Suspicious emails are shared on a daily basis on a Microsoft Teams chat channel called “Phishing.”
38. Each week, our CISO Guillaume Le Malet shares a security element (knowledge, good practice) during the weekly meeting that brings together all the teams, using the main categories proposed by ANSSI.
39. Kraaft printed and posted security best practices on office walls.
40. All employees use the DASHLANE password manager (https://www.dashlane.com/fr) to manage their business logins, with complex passwords that are randomly generated.
41. Source code storage is hosted on Gitlab, via their standard professional service, with Multi-Factor Authentication.
42. In article 11 of our employment contracts, Kraaft has listed a set of professional obligations, including clauses of exclusivity, loyalty, confidentiality, and the return of documents that apply to all employees.
🧱 What are the technologies used in the application?
43. Typescript
44. Frontend: React & React Native in mono-repository (partially shared components and logic)
45. Backend: Node JS, DDD architecture (Domain Driven Design), to properly separate the infrastructure layer (BDD and service providers) and our core business logic 🤖 Do you have APIs? 46. The REST API is currently private: used in integrations like Share Point & Kizeo Forms. We will be exhibiting public APIs in 2025
🔐 This document was updated on October 22, 2025.




